Hacking and Breach Protocol Guide
★ Coming to Switch 2
★ New: Metro System, Car Racing, Romantic Hangouts
★ Phantom Liberty: Dogtown Map & Relics System
★ See our Best Builds here!
┗ HOT: Blades Build, Netrunner Build, & Assassin Build
This is a guide on hacking in Cyberpunk 2077: Phantom Liberty. Read on to learn how to hack, the requirements to hack, and tips and tricks to be a pro hacker!
List of Contents
Major Changes to Hacking in Patch 2.0
Breach Protocol Has Been Reworked
Breach Protocol has been reworked in the latest version of Cyberpunk 2077. As of Update 2.0, Breach Protocol will no longer work on enemies. Any perks related to Breach Protocol from previous versions of the game have also been removed completely.
Now, Breach Protocol is only used when hacking terminals and computers for resources, solving encrypted shards, and opening Airdrops.
Quickhacks are Now Traceable
Due to the Netrunning Update, most Quickhacks are now traceable when used. This means that whenever you use a quickhack to start a battle, a Trace Progress bar will appear on screen.
When the Trace Progress bar fills up, you will be detected by enemies scanning for your presence. There are a few ways to stop the Trace Progress bar, with the most common being killing all enemies in the area.
How to Hack
Requires a Cyberdeck

This is a netrunner's tool of the trade. Any hacker will need a cyberdeck to pull off even the simplest of hacks. Each Cyberdeck will have an amount of RAM, a set of pre-installed hacks, and slots for equipped hacks.
Hacks Costs RAM
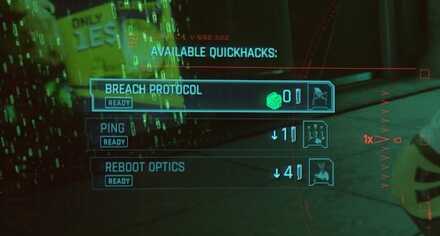
If you compared Cyberpunk 2077 to a traditional RPG, then hacking is like spells, and RAM is mana. Most quickhacks will have a RAM cost, which will increase based on how powerful the hack is. You can increase RAM by buying better Cyberdecks and increasing your Intelligence. You can ever lower the cost with some Perks. Don't worry about running out of RAM, it regenerates outside of combat.
List of Intelligence Perks (Skills)
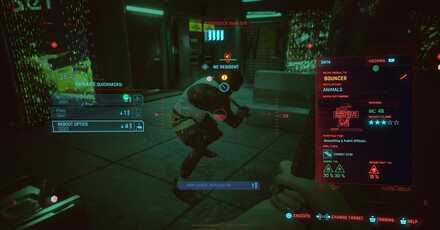
Scan to Select Target
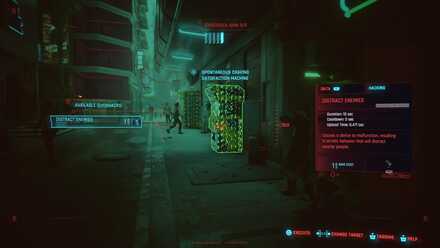
To hack something in the first place you will need to scan enemies or hackable objects. Once you have a target you will be shown your usable hacks, their cost, stats, and effects. Choose the hack you want to use and watch the magic happen!
Breach Protocol Guide

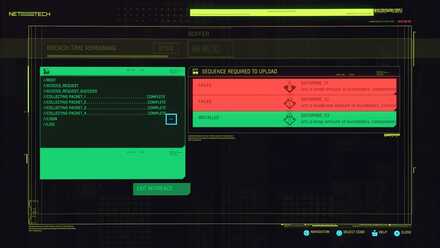
One of the Quickhacks available is Breach Protocol, which has a specific minigame associated with it. You will be shown a grid of numbers and letters and an input buffer with limited inputs. The goal is to activate a daemon by inputting the correct combination into your buffer. Be quick, as there is a timer that starts after selecting an input.
You will need to choose a cell from the top row. After selecting the input, the column that cell is located in will be highlighted and available for selection. You can only select an input from the highlighted row or column, so plan your route out carefully to avoid blocking your own completion route.
This will continue until you run out of inputs in the buffer, or you have successfully activated or failed to activate all of the available daemons.
Much of this is RNG based, but if your buffer size is higher then you can afford to input the wrong cells to get to the combination you need.
A simple example situation could look like this:
| Cells | Daemon |
|---|---|
| 55 1C E9 | ICEpick |
| 1C E9 1C | Mass Vulnerability |
| E9 1C 55 | Turret Shutdown |
In order to activate all three daemons at once, you would need to search for a sequence that allowed you to go in this order:
| 55 1C E9 1C 55 |
Some access points will have a larger amount of rows, columns, and cell options, though, so there will be times where it isn't possible to get every daemon without backing out and trying again. The below recommended perks and upgrades will also increase your chances of being able to get multiple daemons in one go. Activating 3 at once will also earn you the Christmas Tree Attack trophy.
The Only Perk that Affects Breach Protocol in 2.0 is Forcekill Cypher
Given the sweeping changes to netrunning made to Cyberpunk 2077 after Update 2.0, the only perk left that directly affects Breach Protocol is the Forcekill Cypher perk. When obtained, it reduces sequences by 1.
2.0 Forcekill Cypher Perk Effects
Hacking Tips and Tricks
Upgrade Your Cyberdeck

Hacking costs will increase the further you get into the game. This can make even the most basic hacks even harder to activate on enemies. As you progress you will want to upgrade your Cyberdeck to keep up with the costs.
Breach Protocol Access Points for Money and Quickhack Components
Finding Access Points to hack with Breach Protocol is a great way to earn some easy money, as well as Quickhack Components used for crafting Quickhacks. Going for the Datamine V3 will be more difficult, but the payout will be worth it.
Cyberpunk 2077: Phantom Liberty Related Guides

All Tips and Tricks Guides
2.0 and Phantom Liberty Guides
- How to Get Vehicles for Free
- All Phantom Liberty Endings
- How to Get the Tower Ending
- How to Get the King of Swords Ending
- How to Get the King of Wands Ending
- How to Get the King of Pentacles Ending
- How to Get the King of Cups Ending
- How to Purchase Vehicles
- How to Get Capacity Shards
- How to Play Trauma Drama and Rewards
- Should You Help Songbird or Reed?
- How Long To Wait for Songbird
Character Building
- Character Creation Guide
- Best Starting Attributes
- Best Perks by Playstyle
- How to Get Perk Points Quickly
- How to Level Up Fast
- Weapon Customization Guide
- How to Respec
- Which Gender to Choose?
Gameplay Guides
- Beginner's Guide
- Battle System and How to Fight
- How to Get Money (Eddies) Fast
- How to Raise Street Cred
- Missables and Unrepeatable Events
- Stealth Guide
- Hacking and Breach Protocol Guide
- List of Free Cars and Locations
- How to Drive Cars and Bikes
- How to Escape the Police
- How to Avoid Being Hacked
- How to Store Items
- Double Jump or Super Jump?
- Ripperdoc Locations and Cyberware List
- List of Tarot Cards and Locations
- How to Increase Carrying Capacity
- How to One-Shot Every Enemy
- Where To Find Skill Shards
- Where To Find Perk Shards
- How To Duplicate Items
- Which Weapons and Clothing to Keep?
- Bounty Hunting
- List of Radio Stations
- Skill Progression Tier List
- Is Dual Wielding Possible?
- List of Missable Quests and Side Gigs
- All Missable Weapons
- How to Get Carrying Capacity Shards
Best Gear Guides
Story Completion
- How to Start the Phantom Liberty DLC
- All Game Endings and How to Unlock
- How to Get The Devil Ending
- How to Get The Temperance Ending
- How to Get The Star Ending
- How to Get The Sun Ending
- How to Get the Secret Ending
- Romance Guide
- How to Get 100% Clear
- Best Side Jobs to Complete
- How to Get All Johnny Clothes
- All Choices and Effects
Just for Fun
- How to Play the Doom Easter Egg
- List of Hairstyles
- Easter Eggs and Cameos
- Console Commands and Cheats
- The Sixth Attribute
- Joytoy Locations
- New Apartment Locations and How to Unlock
- Slang Explained: Dictionary of Night City Street Talk
- How to Get Nibbles the Cat Pet
- All Binocular Locations
All Cyberpunk 2077 Guides
Comment
There's this site: https://cp2077breacher.com/ where you can automatically solve the breach protocol as well
Author
Hacking and Breach Protocol Guide
Rankings
- We could not find the message board you were looking for.
Gaming News
Popular Games

Genshin Impact Walkthrough & Guides Wiki

Honkai: Star Rail Walkthrough & Guides Wiki

Arknights: Endfield Walkthrough & Guides Wiki

Umamusume: Pretty Derby Walkthrough & Guides Wiki

Wuthering Waves Walkthrough & Guides Wiki

Pokemon TCG Pocket (PTCGP) Strategies & Guides Wiki

Abyss Walkthrough & Guides Wiki

Zenless Zone Zero Walkthrough & Guides Wiki

Digimon Story: Time Stranger Walkthrough & Guides Wiki

Clair Obscur: Expedition 33 Walkthrough & Guides Wiki
Recommended Games

Fire Emblem Heroes (FEH) Walkthrough & Guides Wiki

Pokemon Brilliant Diamond and Shining Pearl (BDSP) Walkthrough & Guides Wiki

Diablo 4: Vessel of Hatred Walkthrough & Guides Wiki

Super Smash Bros. Ultimate Walkthrough & Guides Wiki

Yu-Gi-Oh! Master Duel Walkthrough & Guides Wiki

Elden Ring Shadow of the Erdtree Walkthrough & Guides Wiki

Monster Hunter World Walkthrough & Guides Wiki

The Legend of Zelda: Tears of the Kingdom Walkthrough & Guides Wiki

Persona 3 Reload Walkthrough & Guides Wiki

Cyberpunk 2077: Ultimate Edition Walkthrough & Guides Wiki
All rights reserved
CD PROJEKT®, Cyberpunk®, Cyberpunk 2077® are registered trademarks of CD PROJEKT S.A. © 2020 CD PROJEKT S.A. All rights reserved. All other copyrights and trademarks are the property of their respective owners.
The copyrights of videos of games used in our content and other intellectual property rights belong to the provider of the game.
The contents we provide on this site were created personally by members of the Game8 editorial department.
We refuse the right to reuse or repost content taken without our permission such as data or images to other sites.


























8134826626